Cyber attacks are a powerful weapon not only in international conflicts, but also in the private sphere. Hackers are constantly improving their attacks and it is very difficult to keep up with them. Meanwhile, attacking internal systems or misusing sensitive data can be devastating for some companies. So, what is the best way to prevent cyber crime and what to do if hackers attack your company?
The coronavirus pandemic has moved even previously sluggish companies into the online space. Today’s digital world is increasingly having to deal with its flip side. According to data from Check Point, the number of cyber attacks on Czech companies in 2021 increased by half compared to the previous year, with an average of over 1,000 attacks per week, higher than the global average. Cyber crimes are therefore steadily increasing, and this negative trend has been compounded by the complicated geopolitical situation related to the war in Ukraine.
As a result, more and more companies are realising that a cyber attack could be fatal. According to the Allianz Risk Barometer 2022, a survey of the biggest risks to businesses, experts from more than 100 countries around the world ranked the cyber threat as the biggest danger this year and last year, surpassing even the risk of potential business disruption or the impact of legislative changes.
Therefore, company management should not rely on simply avoiding a cyber attack, not least because it is ultimately the statutory body that is responsible for setting an appropriate strategy to eliminate potential risks. Thus, the management should take sufficient measures to prevent cyber attacks. The opposite situation may constitute a breach of the statutory bodies’ duty of care and their liability for damage suffered.
Hello, send me the money
Statistically, the most common type of cyber incident is phishing, an attack where attackers target individual users. They can steal passwords or credit card numbers or other sensitive data. It is no longer the case that you will receive an email with poor Czech in which you are approached by a Nigerian prince or a supposed friend asking for money. And while such attempts are now more likely to raise a smile, hackers still benefit from the fact that the biggest weakness in these cases is the human link.
Moreover, cyber attackers are constantly improving their methods and using more and more sophisticated strategies. They target large companies or government organisations, which themselves have a high level of security. For example, the National Cyber and Information Security Agency (NCISA) warned of two such cases affecting Czech public institutions in early 2022. In both cases, attackers were able to compromise user accounts and send additional phishing messages from them to various domains, including other public institutions. In one of the campaigns, the attacker even camouflaged the attack by following-up on existing communication and sending malicious messages in response to these threads.
You don’t negotiate with criminals?
Cyber attacks in the form of ransomware, i.e., digital extortion, have also been a “popular” method in recent years. Hackers prevent access to data (typically by encrypting it) and demand a hefty ransom from companies for making it available. The fact that a significant number of companies have already encountered such an attack is confirmed by The State of Ransomware 2021 report prepared by the security company Sophos, which monitored the development of ransomware attacks in 30 countries, including hundreds of companies in the Czech Republic.
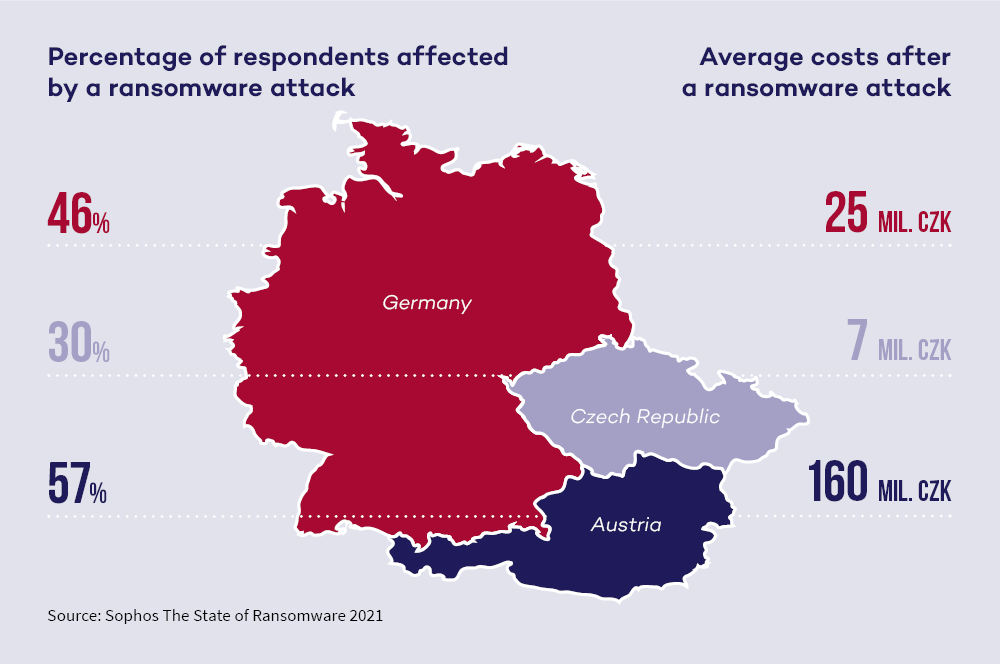
In 2021, attacks of this type affected 30% of the surveyed companies in the Czech Republic and the average negative impact of a ransomware attack was around CZK 7 million. The value includes not only the amount of the ransom, but also the associated costs, employee time and lost profit. In Germany, for example, the figure is CZK 25 million, and the highest value is in our neighbours in Austria, with an average of CZK 160 million. The Czech Republic therefore comes out as the country with the lowest average “amount lost” in the overall ranking, but even so, these are not negligible sums..
Therefore, immediately after the attack, the company management usually addresses the question whether it is worth paying the required ransom. The amount for unlocking systems varies according to the size of the company affected, the difficulty of the chosen attack and, finally, the location of the target. So, whether or not to negotiate is literally the million-dollar question.
For example, in 2018, the US city of Atlanta refused to pay the requested ransom of USD 50,000. For several days, the transport systems were not functional, and officials had to work with traditional paper forms. But the city subsequently paid more than USD 2 million for IT consulting, a security audit and PR services.
Prevention above all
Damages are thus quantified after the battle, and after cyber attacks, companies not only add up the costs spent on restoring and securing systems, investing in cyber security and cyber risk training, but also record the losses caused by slowing or stopping operations or fines for late delivery to contractors. And if sensitive data are leaked, they may also be liable for the loss of confidential business or personal data.
The right defence is the early and preventive introduction of company rules and measures that secure both human processes and the technology and data.
It is therefore best to prevent cyber attacks. The right defence is therefore the early and preventive introduction of company rules and measures that secure both human processes and the technology and data. A good guideline on how to proceed can be the Cyber security Act, which, although it introduces obligations mainly for public entities or their suppliers and operators of key services for the State, the same cyber security rules can be applied in private companies as well. A suitable inspiration is the so-called Minimum Security Standard issued by the Cyber and Information Security Agency.
At the outset, the basis should be a detailed internal analysis of the company that identifies security weaknesses. Knowing these, the company can then work on and eliminate them as part of a comprehensive cyber security and digital protection system. However, it is important that any intended measures are feasible and, above all, understandable to employees so that they know exactly how to avoid risky behaviour.
In addition to this, every company should have proper technical security of systems and data - regularly change passwords to company accounts and systems, use advanced encryption technologies, etc. And companies should also prevent the potential loss of important data and information (which is more common than actual misuse) by correctly setting up backup management.
We also recommend establishing home office security rules beyond the normal procedures. For example, employees should only send work emails via a company email account, use only trusted networks and secure connections to the company network (e.g. VPN connections), etc. Although some rules may sound trivial, they are not always the standard followed.
Companies should also choose their IT systems or anti-virus program suppliers carefully. An appropriate route may be to implement certification according to the ISO/IEC 27000 standards, which set out the requirements for the design, implementation, operation, monitoring and review of an information security management system.
However, putting in place appropriate internal procedures is only the first step. The rules then need to be constantly updated and employees regularly trained to ensure that they actually follow them. This applies not only to prevention, but also to cases where an attack has already occurred.
For such situations, we recommend creating a crisis plan that sets out a clear procedure. Ideally, you should immediately contact legal and security experts directly, who can quickly help to minimise the damage and advise on the necessary course of action. Subsequently, the incident should be properly investigated and documented. If a personal data breach has occurred, there may also be an obligation to notify the Office for Personal Data Protection.

Be careful about contracts
It is also important to make sure that contracts with IT system suppliers, employees and insurance companies are set up correctly. It is advisable to define in detail the obligations related to data protection, encryption, data backup and reporting. Contracts and any internal regulations should always clearly define who has what obligations and who is responsible for what. This is crucial in the event of a real attack, dealing with the consequences and the associated liability.
Contracts with IT system suppliers should ideally guarantee that the systems supplied are regularly updated and that the supplier is sufficiently responsible for ensuring that they actually provide the necessary protection. And contracts with insurance companies also deserve attention. Standard insurance policies of companies often do not cover the risks of cyber attacks, but it is possible to take out special cyber risk insurance, not only for direct attacks on the insured’s computer networks and systems, but also for attacks on cloud services operated by third parties.
Cyber space is a dangerous place, and we believe that a good cyber security strategy is therefore a necessity today. All preventative measures should be seen primarily as a means to reduce future costs that would surely come with a cyber attack if unprepared.
Data is a critical asset, and we help clients protect it. We have logged thousands of hours of legal advice in protecting and valuing data. Need help setting up prevention, remediation after a cyber attack or data loss? Or do you simply want to make better business use of your data? In every situation, we have a practical solution for you. We know this area in great detail. With more than 30 lawyers specialized in information technology law, close cooperation with top forensic experts and renowned technical experts, best practices verified in international transaction environments as well as experience from hundreds of data projects, we can really help and support you effectively in the conceptual handling of your data. We deal in detail with the protection of ICT infrastructure (data storage), including CDNs from a cyber security perspective, and are ready to provide extremely time-flexible support in this area.











